Traceable AI, a startup offering services designed to protect APIs from cyberattacks, today announced that it raised $60 million in a Series B round led by IVP with participation from BIG Labs, Unusual Ventures, Tiger Global Management, and several undisclosed angel investors. The new capital values the company at more than $450 million post-money, and CEO Jyoti Bansal — who’s also the cofounder of BIG Labs and Unusual Ventures — says that it’ll be put toward product development, recruitment, and customer acquisition.
APIs, the interfaces that serve as the connections between computer programs, are used by countless organizations to conduct business. But because they can provide access to sensitive functions and data, APIs are an increasingly common target for malicious hackers. According to Salt Labs, the research division of Salt Security (which sells API cybersecurity products, granted), API attacks from March 2021 to March 2022 increased nearly 681%. Gartner predicts that 90% of web-enabled apps will have more attack surfaces exposed in APIs than user interfaces and that API abuses will become the top attack vector for most companies in 2022.
Bansal saw the writing on the wall four years ago, he said, when he cofounded San Francisco-based Traceable with CTO Sanjay Nagaraj. Bansal is a serial entrepreneur, having cofounded app performance management company AppDynamics (which was acquired by Cisco for $3.7 billion) and Harness (which recently raised a $230 million Series D). Nagaraj, a Harness investor, has long been close within Bansal’s orbit, previously serving as the VP of software engineering at AppDynamics for seven years.
“APIs are the glue that keeps modern applications and cloud services together. As businesses large and small migrate en masse from monolithic to highly distributed cloud-native applications, APIs are now a critical service component for digital business processes, transactions, and data flows,” Bansal told TechCrunch in an email interview. “However, sophisticated API-directed cyberthreats and vulnerabilities to sensitive data have also rapidly increased. Businesses need machine learning here. To have zero trust you need API clarity. You can no longer easily buy or hire security people, so you need to solve these vulnerabilities via technology.”
Like several of its competitors, including Salt, Traceable uses AI to analyze data to learn normal app behavior and detect activity that deviates from the norm. Via a combination of “distributed tracing” and “context-based behavioral analytics,” the startup’s software — which works on-premises or in the cloud — can catalog APIs including “shadow” (e.g., undocumented) and “orphaned” (e.g., deprecated) APIs in real time, according to Bansal.
Traceable describes distributed tracing as a technique involving the use of “agent modules” that collect diagnostic data from within production apps as code executes. Context-based behavioral analytics, meanwhile, refers to understanding the behavior of APIs, users, data, and code as it relates to an organization’s overall risk posture.
“APIs often expose business logic that threat actors use to infiltrate applications and private data. Every line of code needs to be observed in order to properly secure modern cloud-native applications from next-generation attacks,” Bansal said. “Automated and unsupervised machine learning allows Traceable to go deeper and complete the API security requirement better than anyone. As its name suggests, Traceable traces end-to-end application activity from the user and session all the way through the application code.”
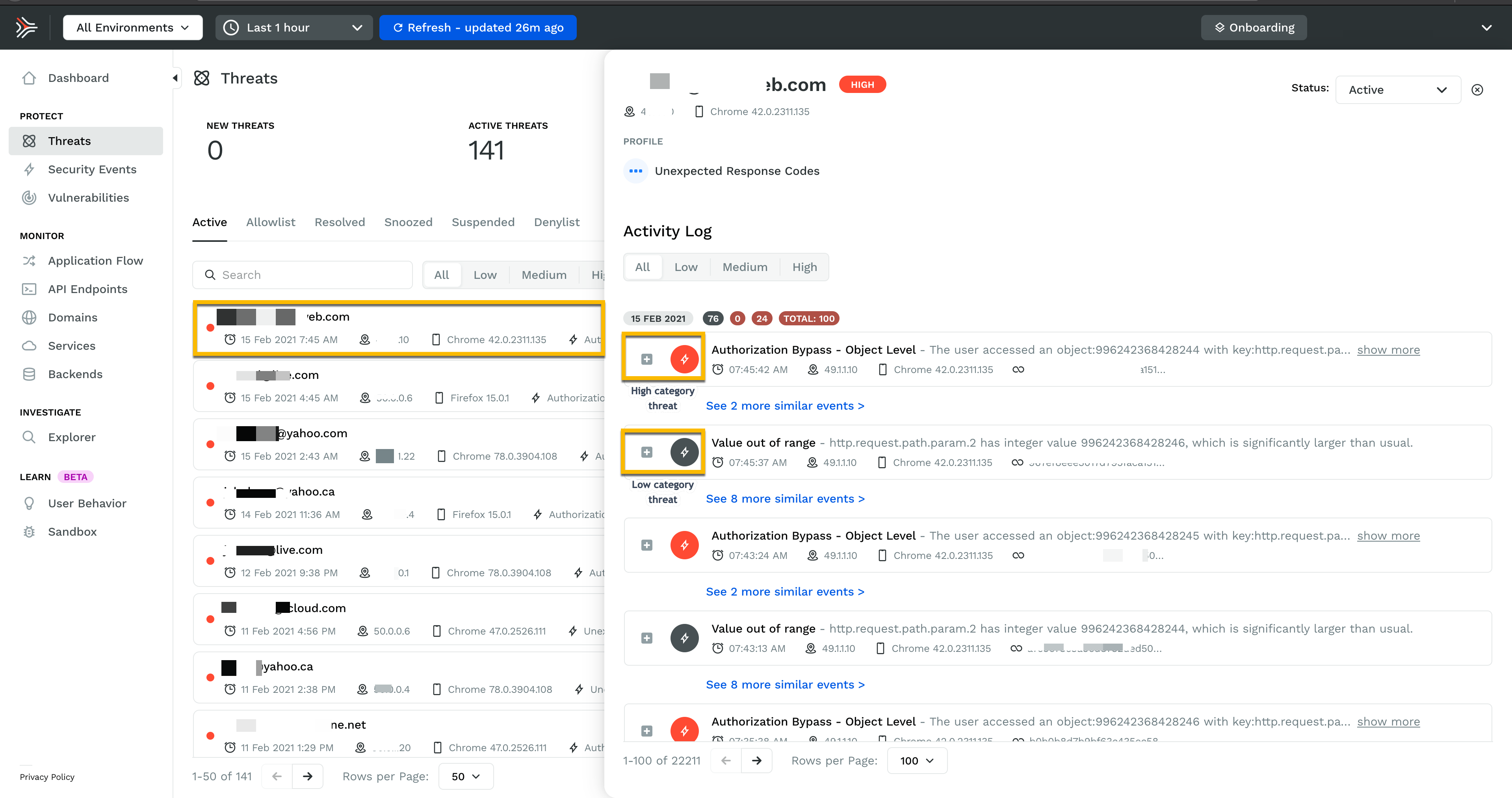
Traceable AI’s monitoring dashboard.
Traceable provides a risk score based on “a calculation of likelihood and the possible impact of an attack,” using 70 different criteria (reportedly). The software also maps app topologies, data flows, and unique security events, including runtime details on APIs and data stores.
The API security solutions market is quickly becoming crowded, with vendors including Cequence, 42Crunch, and Noname Security vying for customers. The growth correlates with the general rise in API usage — particularly in the enterprise. In twin reports, API marketplace RapidAPI found that 90.5% of developers expect to use more or the same number of APIs in 2022 compared to 2021 and that 98% of enterprise leaders believe APIs are a critical part of their digital transformation efforts.
According to Crunchbase data, companies that describe themselves as securing APIs received $193.4 million in venture funding from late 2019 to June 2021, underlining the opportunity that investors see in the technology.
Traceable has done quite well for itself despite the competition. Bansal says that the company has a number of paying customers, and — to spur further adoption — Traceable recently released its tracing technology in open source. Dubbed Hypertrace, it enables enterprises to monitor apps with technologies similar to those powering the Traceable platform.
“The very nature of the pandemic fallout further helped accelerate digital transformation that was already under way. The creation and adoption of millions of microservices and APIs has been a core underlying enabler for the rapid growth of digital services,” Bansal said. “As different organizations have either created, adopted, or used millions of … APIs, it has greatly increased the attack surface vulnerable to API based attacks which cannot be detected or stopped by traditional security solutions. This problem requires a completely new approach to detect and stop these new attacks.”
While Bansal declined to reveal annual recurring revenue when asked, Traceable’s total capital stands at $80 million — the bulk of which is going toward supporting product development and research, he said.
“Businesses use Traceable’s rich forensic data and insights to easily analyze attack attempts and perform root cause analysis,” Bansal continued. “Traceable applies the power of machine learning and distributed tracing to understand the DNA of the application, how it is changing, and where there are anomalies in order to detect and block threats, making businesses more secure and resilient.”
Powered by WPeMatico




